Airsight Blogs
4 Types of Malicious Drone Threats (And How to Detect Them)
In the past decade, drones have transitioned from military assets to ubiquitous commercial tools. While they have revolutionized industries like...
Read MoreProfessional Drone Detection: Mobile Solutions for Real-Time Airspace Awareness
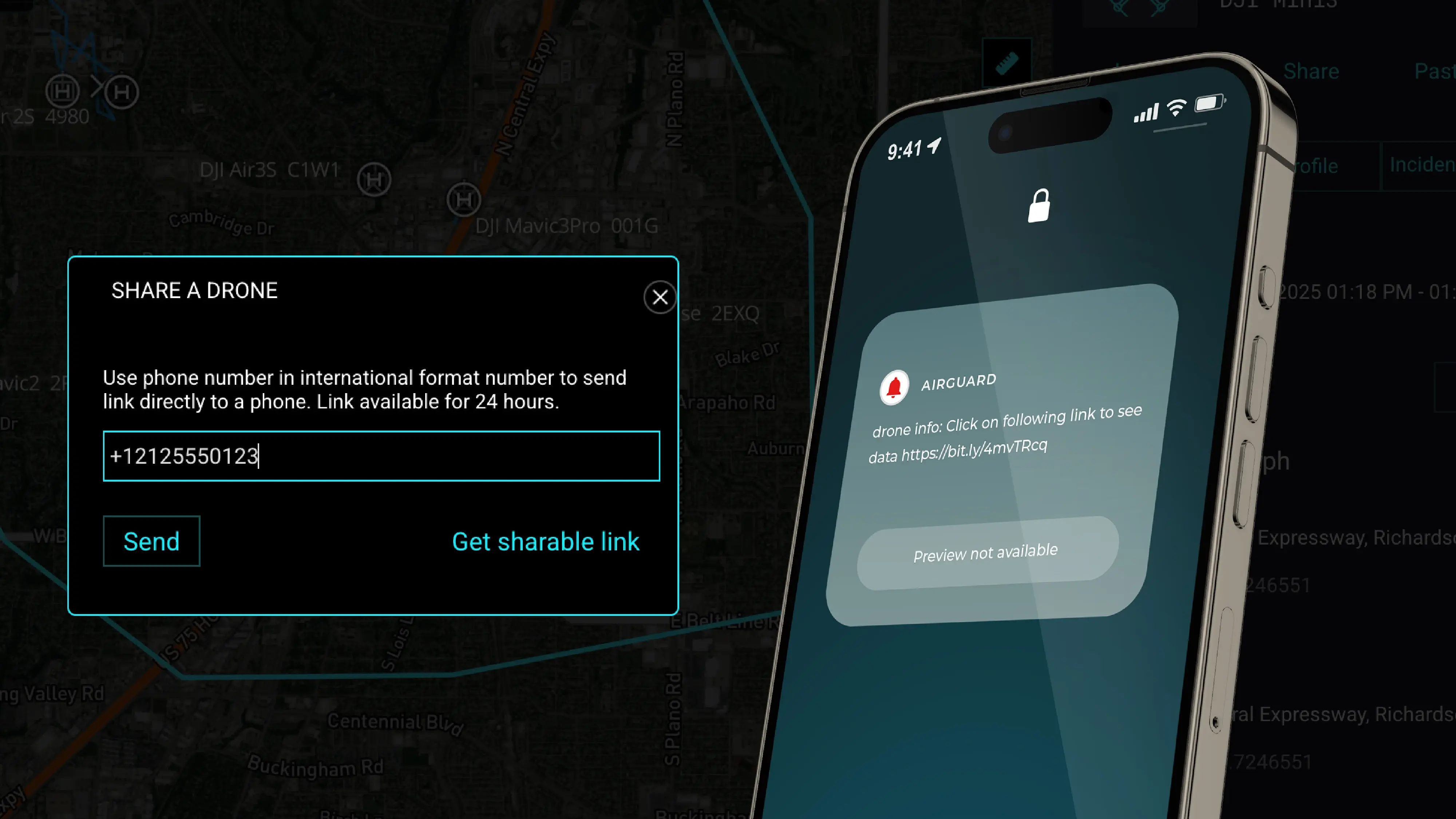
When you see a suspicious drone over your facility or event, your first instinct is logical: you pull out your phone and head to the app store. You...
Read MoreA C-UAS Playbook: How to Protect a Power Plant from Drone-Based Surveillance
For a security director at a power plant or energy facility, the threats are no longer just ground-based. The proliferation of inexpensive,...
Read MoreGlobal Drone Regulations: A Comparison of EU/UK and US Drone Laws
As the drone industry evolves at a rapid pace, the global regulatory landscape is struggling to keep up. For organizations focused on security and...
Read MoreA Drone Crashes in Your Stadium. Are You Legally Covered?
As North American cities prepare to host the largest international sporting events in history, security is at the top of every city, state, and...
Read MoreNew $1B FEMA Funding for World Cup 2026 & Drone Detection: Apply Now
InPart 1 andPart 2, we covered the foundations of finding and applying for grants. Today, we have an urgent and significant update. On October 28,...
Read MorePosts by Tag
- Drone detection (72)
- Drone Mitigation (43)
- Drone Regulations (26)
- drones (23)
- AirGuard (20)
- Company Updates (15)
- FAA (15)
- Drone Industry (13)
- drone policy (13)
- drone law enforcement (12)
- Remote ID (11)
- drone capabilities (11)
- airports (8)
- Stadiums (6)
- Public events (4)
- Border Security (3)
- Infrastructure (3)
- Prisons (3)
- drones General (3)
- Hardware (2)
- Industrial espionage (2)
- Integration (2)
- Rescue Operations (2)
- drone delivery (2)
- Funding (1)
- Mobile Solution (1)
- Partnership (1)
- Prison smuggling (1)
- Security Cameras (1)
- VIP Security (1)
- Webinar (1)
- World Cup (1)
- hospital (1)

.png)
%20(1).webp)
.jpg)











