Your drone detection system is alerting. Is it the pre-approved drone inspecting your rooftop HVAC unit, or is it the same suspicious quadcopter that’s been probing your fence line every night for a week? In a busy airspace, not all drones are created equal. The key to effective security isn't just detecting every drone—it's managing them with intelligence.
A constant stream of alerts for known, friendly drones can lead to operator fatigue, while failing to recognize a recurring threat can leave you vulnerable. This is where a robust drone management strategy, built on whitelisting and flagging, transforms a reactive system into a proactive, intelligent security tool.
This guide will walk you through the parameters of when to authorize and when to escalate, and show you how easily this is accomplished within the AirGuard platform.
The Whitelist: Managing Your Known Assets
A whitelist is a list of authorized drones that are permitted to fly in your airspace. When a whitelisted drone is detected, it is visually marked as friendly, preventing unnecessary high-priority alarms and allowing your team to focus on unknown contacts.
When should you whitelist a drone?
- Your Internal Fleet: Any drones operated by your own organization for security patrols, infrastructure inspection, or aerial mapping should be the first additions to your whitelist.
- Vetted Third-Party Contractors: You’ve hired a company for a specific task. Their drones should be whitelisted for the duration of the project. Common examples include:
- Media or photography drones for a corporate event.
- Drones conducting a roof or facade inspection.
- Aircraft used for construction progress monitoring.
- Known Neighboring Aircraft: If a trusted neighboring facility operates drones near your property, whitelisting their aircraft can reduce nuisance alerts, provided a formal agreement is in place.
The Flag List: Escalating Suspicious Activity
Flagging is the opposite of whitelisting. It is a feature used to mark a drone that has exhibited suspicious behavior, ensuring it gets immediate and heightened attention any time it appears in the future. This turns every detection of that drone into an intelligence-led event.
What parameters justify flagging a drone?
- Perimeter Testing: A drone that repeatedly flies along a sensitive boundary—like a perimeter fence, a server farm, or executive offices—without ever fully breaching. This could indicate surveillance or testing of your response capabilities.
- Unusual Flight Times: A drone that consistently operates outside of normal business hours, such as late at night or on weekends, could be attempting to avoid detection. AirGuard’s "Drone Insights" feature, which charts activity by time and day, is excellent for identifying this pattern.
- Repeated Altitude or Geofence Violations: A drone that has a history of breaching pre-defined "Alert Zones" for critical areas or frequently violates altitude ceilings (e.g., flying over 400ft for surveillance) poses a higher risk and should be flagged.
- Flights Over Sensitive Areas: An unknown drone that consistently flies over critical infrastructure, employee parking lots, or loading docks warrants extra scrutiny on every subsequent flight.
How AirGuard Makes Drone Management Simple
Theory is important, but execution needs to be effortless. AirGuard is designed to make these critical decisions easy to implement in real-time.
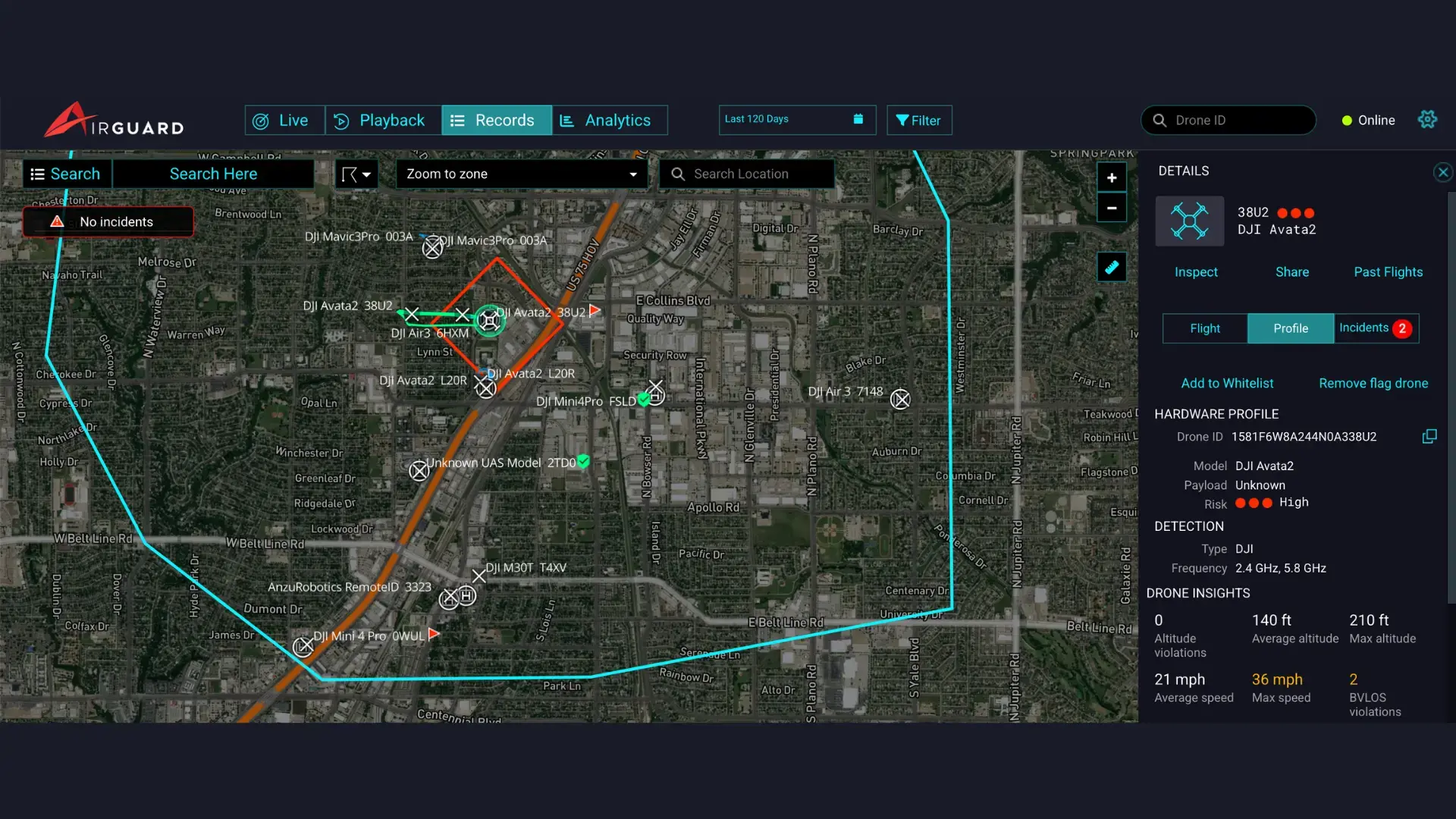
From the Live, Playback, or Records screen, an operator can select any drone to pull up its detailed information. In the
"Profile" tab, they have two simple, one-click options:
- Add to Whitelist
- Flag drone

Once a selection is made, the drone’s icon is immediately and permanently updated across the platform. A whitelisted drone appears with a green check mark, while a flagged drone is marked with a red flag. This provides instant visual context to operators, allowing them to assess the situation in seconds.


From Raw Data to Actionable Intelligence
Effective airspace security is about contextualizing every detection. By implementing a clear strategy for whitelisting friendly assets and flagging suspicious actors, you can dramatically reduce operator workload and improve your security posture. These simple but powerful features elevate your C-UAS program from a simple alerting system to an intelligent, proactive security operation.