Corporate spies and hackers are utilizing drone technology to steal trade secrets, confidential information, and other sensitive data from corporations and data centers. Even the most physically fortified structures have a security gap when it comes to drones, the flying devices can easily penetrate their perimeter security controls.
Across all industries, cyberattacks that manipulate or destroy data are a rising concern. These threats can undermine short-term and long-term corporate business strategies and brand perception. In the wake of many high-profile data breaches and data misuses, consumer trust in companies handling their data responsibly is falling. According to PwC’s 2017 U.S. Consumer Intelligence Series survey, 75% of consumers say they do not believe most companies handle sensitive personal data responsibly.
Nefarious Payloads: Smartphone, Raspberry Pi, Wifi Pineapple, Thermal Imager, Camera, Microphone
Unmanned aircraft systems (UAS), or drones can easily bypass physical security measures leaving companies vulnerable to attacks. Drones are discreet and capable of carrying nefarious payloads over fences and next to structures.
Drones can carry a payload intent on hacking your company, such payloads include a smartphone, Raspberry Pi, or Wifi Pineapple device. Hackers can use these devices to intercept or disrupt data communications or hack into servers. Wireless, Bluetooth, and RFID signals are all vulnerable to drone cyberattacks. Hacker drones can access signals a traditional off-site hacker could not obtain.
Drones equipped with cameras & thermal imagers can map out the inside and outside of your property with precision. Thermal imagers can detect temperature variations and give heat signatures allowing hackers and spies to locate sensitive equipment such as servers in your facility.
Cameras, thermal imagers, and microphones can also be used in reconnaissance missions to collect intel. Drones can record who is coming and going from the building, identify patterns in security personnel units or other key employees. Drones can be used to peer in windows to record meetings, or to identify any valuable information in plain sight.
When your office is on the 3rd or 10th floor of a building, you don’t really think about people looking and spying through the windows. Essentially, drones put eyes through windows at any floor level. As many corporations already know, competitors will go to great lengths (or “heights” in this case) to gain intel.
Cyber attacks and Industrial Espionage
Drones threats to businesses and organizations:
- Spy on operations
- Gather sensitive intel
- Intercept and steal data
- Infiltrate networks
- Air gap attacks
Cybersecurity threats are advancing due to drones being equipped with more advanced hacking software, and their ability to covertly infiltrate sensitive airspace. Corporations, data centers, research and development labs, basically anywhere with sensitive information or important meetings could be a potential target for hackers or spies. Corporate espionage isn’t something new, drones are just the latest method spies are using to threaten the confidentiality of your company.
Last year, researchers at Ben-Gurion’s cybersecurity lab devised a method to penetrate the “air gap” security safeguard. The team successfully hacked into air gapped system using a drone. The team exploited the hard drive LED indicator light to access data from the computer. The team planted malware in the target computer - which could easily be accomplished by an insider. The infected computer leaked sensitive data in each LED blink to any spy with a line of sight to the target computer.
Corporations such as Apple, Facebook, and Tesla, among others, have experienced public incidents of drones conducting aerial espionage. Earlier this year, a drone crashed onto Apple Park Campus, even though Apple had previously declared the campus a “No Drone Zone.” If you want to know what the Tesla factory is up, you can google Tesla factory drone footage and find a number of videos.
Cost of IT Downtime
According to The Ponemon Institute’s downtime study, released in January 2016, a data center outage costs around $9,000 per minute. The study also revealed the average outage lasted 95 minutes, making the average data center outage cost $855,000.
Even if you aren’t a data center, IT downtime is still very costly. Gartner estimated that the average unplanned network downtime costs an enterprise approximately $5,600 every minute.
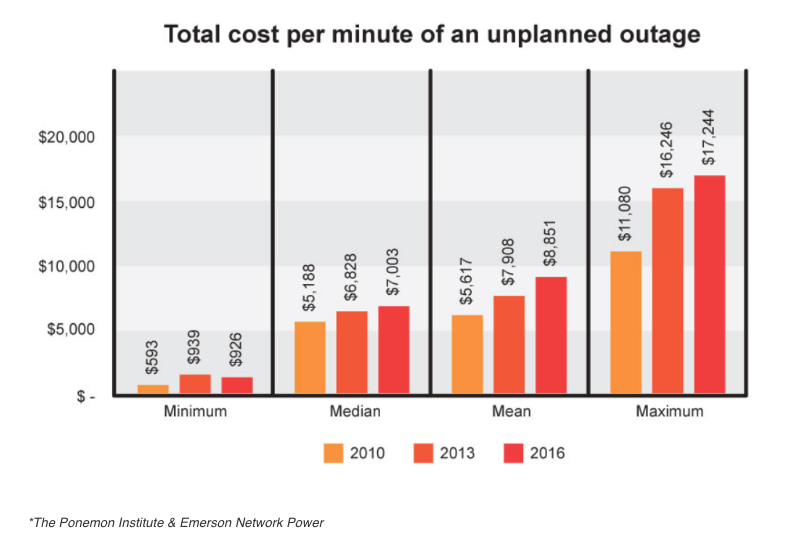
The U.S’ National Cyber Security Alliance found that 60 percent of small companies are unable to sustain their businesses over six months after a cyberattack. According to the Ponemon Institute, the average price for small businesses to clean up after their businesses have been hacked stands at $690,000; and, for middle market companies, it’s over $1 million.
Cyberattacks account for 22% of the root cause for downtime at data centers, and cyber crimes are the fastest-growing cause of outages. Drones have the unique capabilities of delivering cyber or physical attacks - they can hack your data or attack your rooftop cooling systems.
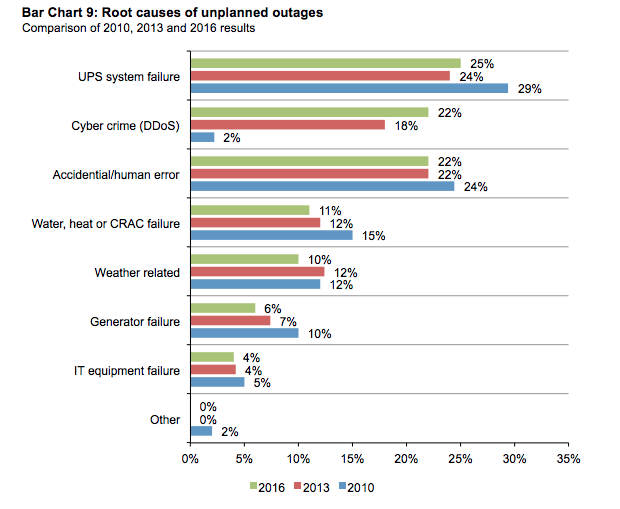
No industry or organization is immune to drone threats, and perimeter security controls are not enough to safeguard vulnerable airspace. Safeguards must be in place to prevent loss or theft of sensitive corporate data and protect your organization’s most valuable assets - the personal information and the trust of your customers.











